KB5014754
Page updated: 2025-02-26
Background
In spring 2022 Microsoft released KB5014754. This fix addresses vulnerabilities CVE-2022-26931 and CVE-2022-26923
Uppdate in September 2024 from Microsoft
Changed the Full Enforcement mode description in the "Timing for Windows updates" section to reflect new dates. February 11, 2025 will move devices to Enforcement mode but leave support to move back to Compatibility mode. Full registry key support will now end September 10, 2025.
NOTE
Check for warnings/errors in the event log on you domain controllers
Activate "Compability Mode"
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Kdc
StrongCertificateBindingEnforcement=0
# If you install KB5014754 on your domain controllers, the certificates that do not meet what Microsoft calls "Full Enforcement Mode" are logged.
# "Full Enforcement Mode" will be required from February 11, 2025.
# Note that "Disabled Mode" could only be used until April 11, 2023.
Note: If you do not act before these dates, you will not be able to log into Windows with certificates that only contain the UPN in the SAN
There are several different ways to tackle this. Which method you choose depends on the context.
A) The "SID method" - Variant 1 - With an underlying AD
1. Install KB5014754 on domain controllers and on the MSCA machine.
2. Ensure that your certificate management system is properly configured and then allow all users to have new certificates issued according to the desired process.
3. The certificate is then provided with a new field with a special OID (1.3.6.1.4.1.311.25.2) where the user's SID from AD is added.
The mapping between certificate and AD account is now based on the users' respective SIDs.
Note 1:
If you use Net iD Portal 5.8.x in combination with a properly configured enrollment agent, you do not need to upgrade to 5.8.5.
Note 2:
Of course, this method does not work in PKI solutions where the certificates are issued without contact with an underlying AD.
Example with the correct OID and SID as value:
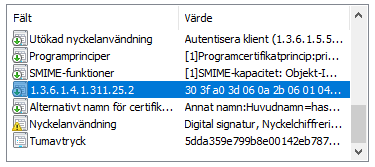
B) "SID method" - Variant 2 - Without an underlying AD
1. Install KB5014754 on domain controllers and on the MSCA machine.
2. Install Net iD Client 1.3 on the clients where cards are issued.
3. Install Net iD Portal 5.8.5
4. Ensure that your certificate management system is properly configured and then allow all users to have new certificates issued according to the desired process.
5. The certificate is then provided with a new field with a special OID (1.3.6.1.4.1.311.25.2) where the user's SID from AD is added.
Note:
In order for the correct SID to be retrieved, it is assumed here that the card handler himself is logged in to the AD in which the card recipients are located. In this variant, it is the Net iD Client/Enterprise that retrieves the SID from AD for the current user in a way that corresponds to what can be done with the following command:
C) "The mapping method (SKI)"
Certificate mapping has existed for years and of course you can script the correct values into the altSecurityIdentities attribute for all user objects in AD.
- If you have something absolutely unique in Subject (e.g. SubjectSerialNumber=personal identification number/employment number/hsaid) you can map to it. Then AD does not need to be updated when a new certificate is issued to the user. However, it is classified as "Weak" so that variant goes away.
- If, on the other hand, you choose to map to the certificate's serial number, you must remember to update the user objects (altSecurityIdentities) in AD with the correct serial number in connection with for example reserve card issuance. Classified as "Strong".
- Inera has produced an instruction for the mapping method in a SITHS context: https://inera.atlassian.net/wiki/x/swL7pw, all certificates are found in the HSA directory. A little tinkering but it works.
Customers who run Net iD Portal and have few users can, of course, relatively easily replace all certificates with ones provided with SIDs. But not infrequently, the number of users is so large that it is not possible to easily replace the certificates on thousands of cards. Then you can choose a combination of certificate mapping and SID, or completely decide to only use certificate mapping. The combination solution means that, from a certain date, all newly issued certificates are provided with SIDs at the same time as they use certificate mapping. Once all certificates are exchanged, one can stop writing mapping information to altSecurityIdentities.
For convenience, we have provided Net iD Portal 5.8.5 with a function to write the correct data to altSecurityIdentities in the user's AD account. The feature can be configured into the appropriate process(es) to incrementally provide users accounts with the correct mapping information, for example in connection with the issuance of reserve cards. However, this is hardly enough and may need to be supplemented by other processes also including updating altSecurityIdentities, e.g. "Update user" in the portal. If you have many users, however, it is not enough if you don't want to sit and click through all the users. Then a data extraction from MSCA or Net iD Portal and a more extensive scripting to all users altSecurityIdentities is simply required.
Note:
We have chosen to use "X509SKI" in Net iD Portal because that value is easier to handle without the risk of various forms of conversion errors. Both "X509SKI" and "X509IssuerSerialNumber" are rated as "Strong" by Microsoft.
Error message examples
The certifikatet can not be verified for some reason =>
Wrong or corrupt SID OID or SID-value =>