macOS
Page updated: 2025-09-05
macOS - Useful commands and file locations
Check installed CTK plugins
pluginkit -m -p com.apple.ctk-tokens
pluginkit -v -m -p com.apple.ctk-tokens
pluginkit -vv -m -p com.apple.ctk-tokens
Smart card commands
security list-smartcards
security export-smartcard
system_profiler SPSmartCardsDataType
Note: Make sure you import all the roots and intermediates to Keychain - System so that
"system_profiler SPSmartCardsDataType" tells you:
SSL trust: YES, X509 trust: YES
Pairing commands
sc_auth list (Check pairing)
sc_auth unpair (Unparing a user)
sc_auth pairing_ui -s status (Pairing dialog status)
sc_auth pairing_ui -s enable (Enable pairing) OR sudo defaults write /Library/Preferences/com.apple.security.smartcard UserPairing -bool false
sc_auth identities (List available smart cards and paired/unpaired identities)
Disable/Read/Delete CTK-modules
sudo defaults write /Library/Preferences/com.apple.security.smartcard DisabledTokens -array com.apple.CryptoTokenKit.pivtoken (Disables the built in PIV-support from Apple to avoid conflict with Net iD PIV-support)
sudo defaults write /Library/Preferences/com.apple.security.smartcard DisabledTokens -array com.pointsharp.netid.client.ctk (Disables Net iD Client CTK-module)
sudo defaults read /Library/Preferences/com.apple.security.smartcard DisabledTokens (Read DisabledTokens)
sudo defaults delete /Library/Preferences/com.apple.security.smartcard DisabledTokens (Delete DisabledTokens => All present modules active)
sudo defaults write /Library/Preferences/com.apple.security.smartcard DisabledTokens -array org.opensc-project.mac.opensctoken.OpenSCTokenApp.OpenSCToken (Disables the PIV-support from OpenSC)
Antivirus makes everything slow
In some cases your antivirus software can make reading/using certificates very slow, for example with Microsoft Defender for macOS.
Try to exclude this from scanning:
/Applications/Net iD.app/Contents/PlugIns/CryptoTokenKit.appex/Contents/MacOS/CryptoTokenKitKit
Tokend
sudo defaults write /Library/Preferences/com.apple.security.smartcard Legacy -bool true (Enable tokend. Not possible on macOS 11 (Big Sur))
sudo defaults write /Library/Preferences/com.apple.security.smartcard Legacy -bool false (Disable tokend)
sudo defaults read /Library/Preferences/com.apple.security.smartcard (Check status of com.apple.security.smartcard)
FileVault 2
FileVault does not support smart cards for authentication, meaning you will still need to use your password to unlock your FileVault-encrypted disk. By default, when a user enters their password to decrypt the FileVault disk at boot, this password will be passed through and a smart card will not be used for login,even if you configure it to be required. To change this so that the user will not automatically be logged in and will be shown the login screen, run the command below in Terminal.
sudo defaults write /Library/Preferences/com.apple.loginwindow DisableFDEAutoLogin -bool YES
File locations
/usr/local/lib/netid/* (Net iD Client)
/usr/local/bin/ (netid -command) (netid -dialog test)
/etc/netid.conf (Net iD Client global configuration) (Not relevant for CTK-module but for Net iD Client itself and it's WebExtensions)
/Users/[user]/.netid (Net iD Client "user configuration")
/Applications/Net iD.app/Contents/PlugIns/CryptoTokenKit.appex/Contents/Resources/netid.conf (Net iD Client global configuration for CTK-module)
/System/Library/Frameworks/PCSC.framework/PCSC (PC/SC, not used by CTK-module)
/usr/libexec/SmartCardServices/drivers/ifd-ccid.bundle /usr/libexec/SmartCardServices/drivers/ifd-ccid.bundle/Contents/version.plist /usr/libexec/SmartCardServices/drivers/ifd-ccid.bundle/Contents/info.plist
Chrome - Extensions: /Users/[user]/Library/Application Support/Google/Chrome/Default/Extensions/ Edge - Extensions: (edge://version/) /Users/[user]/Library/Application Support/Microsoft Edge/Default/Extensions/
Firefox - Extensions: /Users/[user]/Library/Application Support/Firefox/Profiles/[user-profile-name]/extensions/
Trace - Non CryptoTokenKit related events
Trace can be enabled by editing /etc/netid.conf, the trace file will be found here:
/tmp/netid.txt
Trace - CryptoTokenKit related events
Example path will depend on macOS version
macOS 14 Sonoma
/Users/[username]/Library/Containers/com.pointsharp.netid.client.ctk/Data/tmp/netid.txt
macOS 13 Ventura, macOS 12 Monterey and macOS 11 Big Sur
/var/folders/xx/yyyy/T/com.pointsharp.netid.client.ctk/netid.txt
Use "set" to see the location for "TMPDIR" where the "CTK-trace" is.
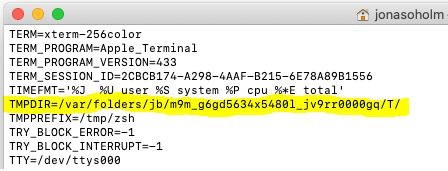
Find CTK sandbox for "all users", i.e. fetch things happening pre-login
sudo find /var/folders -name "netid.txt" 2>/dev/null
Signature check
codesign --verify --verbose Net\ iD.app Net iD.app: valid on disk Net iD.app: satisfies its Designated Requirement
codesign --verify --verbose CryptoTokenKit.appex CryptoTokenKit.appex: valid on disk CryptoTokenKit.appex: satisfies its Designated Requirement